Heart Bleed for Heart Beat
|
11 years ago 6 |
20140421
Environment:
LinuxMint 13 Maya - Cinamon 3.2.0-23-generic x86-64 GNU/Linux
Audience: Newbies, End Users - (*u1)
Purpose: Simple, short and easy explanation for mere mortals. Driving out fears and confusions (*u1)
For: Users Desktop systems (openSSH / openSSL Client) - (*u1)
NOT for: Servers. As this only outline the Initial steps, there are other steps to be taken on Servers - (*u1)
Why: I had the same confusion, googled and piece up this "semi-why, what and how-to" - (*u1)
Overview: The Heartbleed Bug is a serious vulnerability that allows outside attackers to steal sensitive information on an otherwise believed to be secured connections for example: https (ie: http over ssl/tls), secure email and VPN. All done without leaving a trace.
For more details: http://heartbleed.com/ ; Also at My Blog with easy formatting - (*u3)
Background: I am running different versions of OpenSSH/OpenSSL on Linux, Desktop, Servers, and Network Devices. Basically, I ssh back into them. - (*u1)
Disclaimers: If I have hindered your quest and progress to fix this issue, accept my apology. If I have further confused you, I seek your advise to improve upon this "Article". Thank you :)!! - (*u1)
Quick Summary: - (*u2)
-
How to Check
- openssl version -a
- look for build date on/after: 7apr2014
-
More Checking
- apt-get changelog openssl
- apt-get changelog libssl1.0.0
- look for CVE-2014-0160 fix
Status: Done and Ready
Updates:
*u1 - inserted on 20140426
*u2 - inserted a "Quick Summary" on 20140426, if you do not want to read the details
*u3 - 20140427: A simple overview
*u4 - 20140427: It should have been 1.0.2-beta Testing Branch, instead of 1.0.2 Alpha Testing Branch as stated before this update.
Heart Bleed Bug
-
What ain't Broken?
-
What is Broken?
-
What is fixed?
What was Not Broken by Heart Bleed?
-
Major Components
-
SSL
-
SSH
-
Heart Beat
-
-
OpenSSL before 1.0.1
-
Non OpenSSH/OpenSSL implementations
What is Broken?
-
OpenSSH/OpenSSL Heart Beat implementation
-
1.0.1 Branch
-
1.0.2-beta Testing Branch - (*u4)
-
-
Yep, it's an Implementation error
What is fixed?
-
OpenSSL v1.0.1g
-
Open SSL 1.0.2-beta2 - (*u4)
-
Distropatch by each distro
-
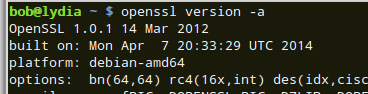
Built on/after 7apr2014
-
These not necessary be 1.0.1g
-
-
How to check?
-
openssl version -a
-
Look for build date
-
Some more Checking?
-
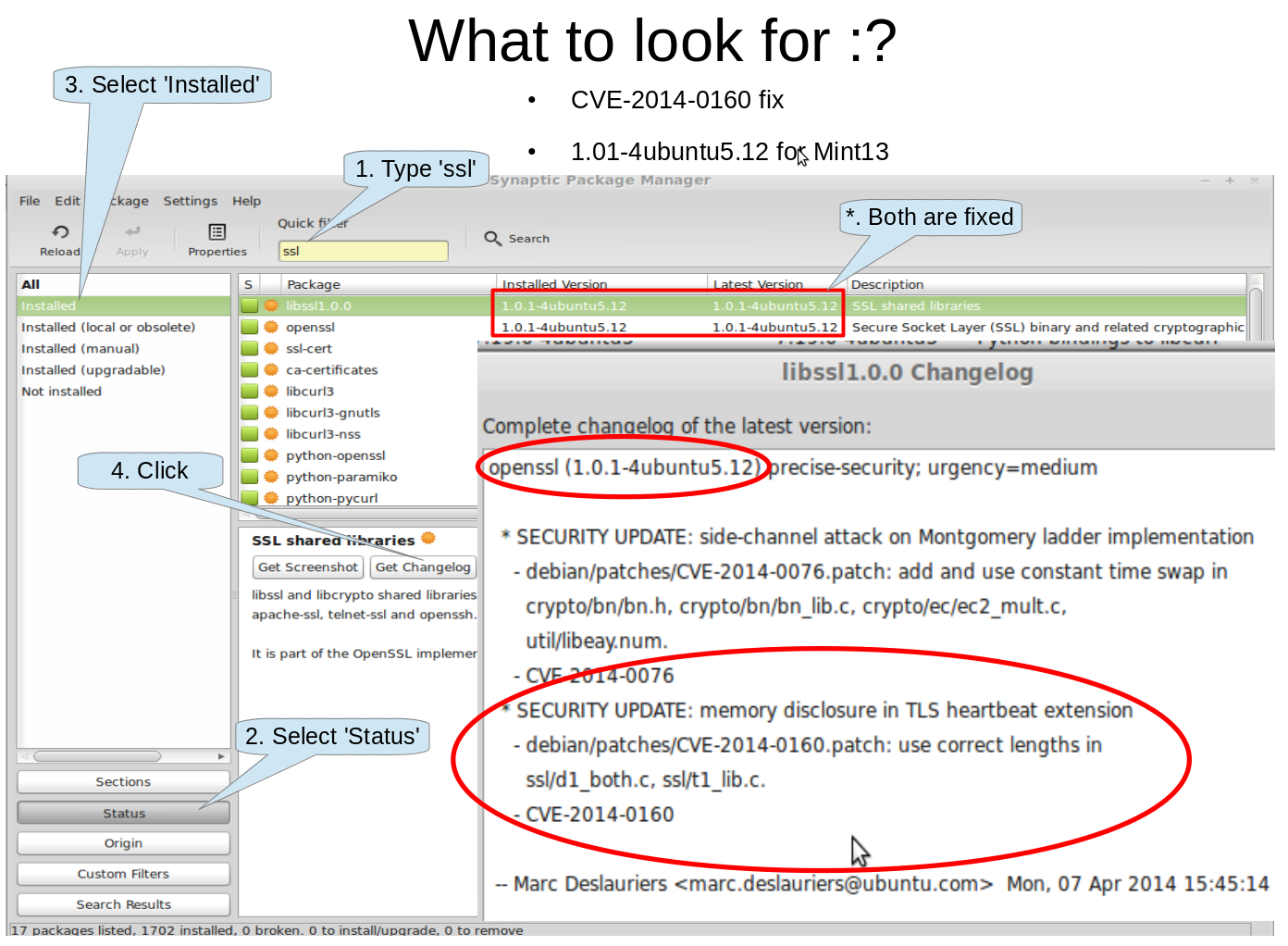
Launch Package Manager
-
Eg: Mint Synatic Package Manger
-
-
Search/Filter for “ssl” installed
-
Eg: libssl1.0.0, openssl
-
-
Select libssl1.0.0 and [Get Changelog]
-
Look for CVE-2014-0160 fix
-
-
CLI - Mint13
-
apt-get changelog openssl
-
apt-get changelog libssl1.0.0
-
What to look for :?
-
CVE-2014-0160 fix
-
1.01-4ubuntu5.12 for Mint13
Anything Else?
-
Yes, Google for the rest :)
-
This is meant As a Simple Guide
-
For more details eg: Server ... pls Google or seek Professional help - (*u1)
-
-
After Patch, Look for??
-
Generate New Certificates - if running Server - (*u1)
-
Revoke Old Certificates - if running Server -(*u1)
-
Get all End users to Change Passwords
-
Other Details
-
Check with your Service Provider eg: Online Mail, Ruby Rail etc...
-
-
-
Remember not all OpenSSH/OpenSSL is affected!
Comments
Acknowledgement
I would like to thank Hammer459 for his constructive feedback which enable me to improve this 'mini-tutorial' / article. Now, it is put into much better perspective in term of scope and formatting for readability.
Once again, thank you.
Hi Hammer459,
Thanks for the feed back. Sorry that the article do not have the breadths and depths that you expected.
Done some modification and update (*u1) to put this article into perspective.
Yes, it might be poorly formatted but how could I improve it so that it is not a spam anymore?
Once again, thank you :)
Bob